Estimated Reading Time: 13 minutes
A Brief Look Back at 2018
2018 has been a wild year for technology and the internet. The year kicked off with the announcement that the industry-leader, Intel, had major security flaws (Meltdown & Spectre) in their chip architecture. As we now know, the performance boosts from speculative execution—also enjoyed by most of the industry—have some significant security pitfalls. Pitfalls we’ll be coping with for the next several years thanks to years-long product development cycles.
That’s just the beginning. In February, GitHub was hit with the most powerful DDoS attack to date. Peaking at over 1.35 terabits per second, the ante has been upped. Malicious cryptocurrency mining overtook ransomware as the de facto malware threat in terms of prevalence—while mobile phishing continues to evolve as one of the most effective attack methods.
“According to a Verizon Data Breach Investigations Report, 30% of phishing messages are opened by targeted users—and 12% of those users click on the malicious attachment or link.”
Source: Verizon Data Breach Investigations – blog.dashlane.com
It was also another long year of data breaches. Though, thanks to the implementation of the EU’s General Data Protection Regulation (GDPR) in May, businesses and enterprises have begun responsibly disclosing breaches—if only to avoid the hefty fines associated with non-compliance or covering them up. The list goes on and on. IoT security vulnerabilities, new & growing botnets, router vulnerabilities, we’ll just stop there.
Through all of this, there’s an ongoing skills shortage for cybersecurity professionals. We just simply cannot keep up with the rapid rate of change. In September of 2017, the International Info System Security Certification Consortium (ISC2) projected a shortfall of 1.8 million cybersecurity workers by 2022 (reported by CSO). A short year later, the ISC2 estimates that we’ve already surpassed that number, at that the shortage is already nearing 3 million. As a society—individuals, businesses, and even government bodies, are simply not equipped to properly defend against the current threat climate.
And so we turn our attention forward. What’s in store for 2019? We don’t have a magic 8-ball, but we believe that over the next year, these are the trends that will continue to shape our lives. Yes, it’s really that serious. These trends impact business costs, ad revenue, and regulations made by our governing bodies—which in turn contributes to changes in trade and foreign affairs…
Okay. It’s not that dramatic. But at the same time—it kind of is.
Cybersecurity & Tech Predictions for 2019
Increased Demand for “Serverless”, FaaS, and Cloud Provider Security
Spurred on by the “Serverless” movement and FaaS trends (that’s Function-as-a-Service)—security operations are increasingly being abstracted away from the traditional concepts of on-premises, data center, and even virtual environments on cloud machines that execute critical business operations. Instead, those functions can be executed by leasing computation time from a cloud provider—minimizing both required upfront capital costs, as well as maintenance and personnel costs that effectively achieve the same tasks.
And many of those tasks, including general maintenance, no longer require direct intervention from in-house IT personnel. Instead, the responsibility of securing infrastructure (and data), managing equipment, and technical support shift to cloud providers like Amazon and Google.
With the announcement of widespread security vulnerabilities like Meltdown and Spectre, the entire industry (both good and bad actors) has been spending resources to find weaknesses in the form of backdoors and bugs. As the trend towards FaaS and Serverless computing models continues, we expect a sharp increase in demand and reliance on cloud providers to deliver advanced security solutions. These characteristics come to a head because they not only allow businesses to effectively outsource machines and maintenance costs—but also the associated security costs AND responsibility.
“Zero Trust” & “Post Perimeter” Gain Ground
Businesses are already well aware of the costs associated with security and data breaches. This, combined with the rising impact and widespread integration of non-traditional connected devices (i.e. IoT and mobile) in the workplace, will continue to push businesses into focusing on these “no-longer fringe” devices. In 2018, digital commerce reports that 73% of internet consumption occurs on a mobile device—a rate that going to continue to grow.
Even with the market saturation and slow of smartphone sales in the past couple of years—mobile devices continue to outpace growth of traditional desktop computers and laptops. Over the next several years, it is expected that more employees will perform more daily actions on a mobile device as opposed to a desktop or laptop. And we’ve learned the hard way that those devices—moving from network to network with simplified user interfaces and design choices intended to improve “usability” on smaller screens—are more difficult to secure.
In 2019, expect for cybersecurity trends to focus on mobile devices and the post-perimeter world.
Yes. Even More Data Breaches.
At least, more that we hear about.
GDPR how been in effect now for over six months, sites everywhere have implemented those nagging cookie agreement policies and made a mess of browsing the web. But, it’s not all bad. It’s also forced businesses all over the world to take data management seriously. They’ve had to improve security and infrastructure, define safe data information and storage requirements, outline incident response policies—and perhaps most importantly—it’s given all of us a healthy reminder that we should think about what personal information we share online, and with whom.
Consider, the Marriott/Starwood Hotels data breach from just this year. The personal records of over 500 million customers were compromised in a multi-year persistent breach dating back as far as 2014. We’re prepared to see the number of exposed records continue to increase next year.
Companies are perhaps more aware than they’ve ever been about keeping data secure—and are taking steps to secure their infrastructure against future attacks. And that’s a good thing. But as with Marriott/Starwood breach, and the recent Google data exposures, even if companies can achieve a high level of security, doesn’t mean they won’t find that holes have existed and data was compromised in previous years. For 2019, we’re expecting to—at minimum—a modest increase in data breaches, both in the number reported as well as # of records exposed.
Likely though, it will be a significant increase.
Just to jog your memory regarding data breaches in recent years, here’s a graph from Statista on the largest data breaches to date.
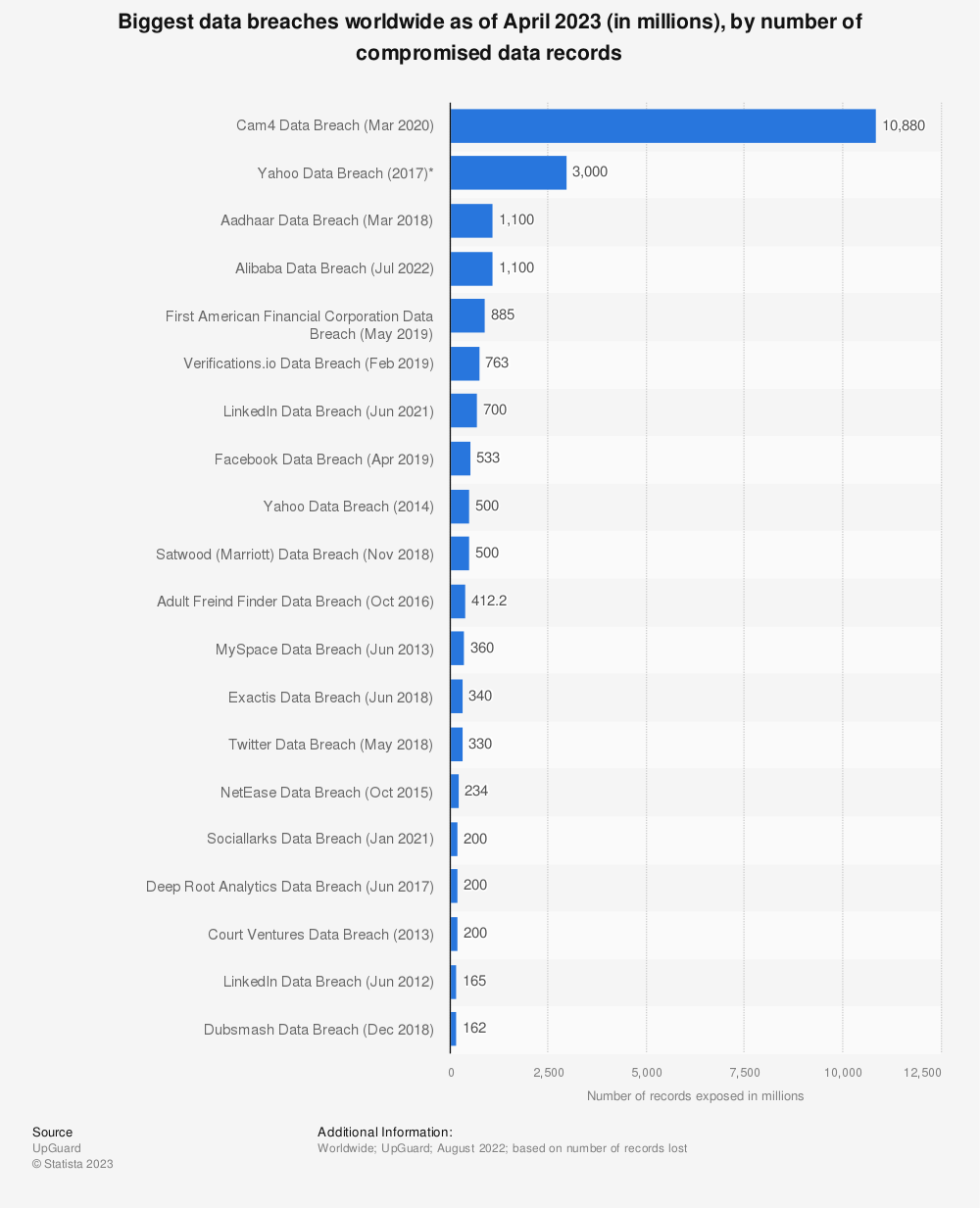
Find more statistics at Statista
Human Error Will Continue to be the Primary Cause of System Intrusions and Data Breaches.
The majority of data breaches and exposures boil down to one thing. Our own propensity for mistakes. That’s right, human error. With the increasing complexity of systems and abstractions—along with the continued siphoning and sale of mass amounts of aggregated data on consumers—we’ve created quite a mess. IT professionals, even the best, are still prone to errors and have accidentally left databases and systems unsecured. Ripe for cyber criminals to pick through.
In a report from the UK’s Information Commissioner’s Office (ICO), the public body responsible for monitoring and fining data breaches, it was found that 88% of UK data breaches were caused by human error, as opposed to intrusion via malicious attack.
Until the dawn of a general artificial intelligence—when a virtual assistant will be able to execute sophisticated commands and properly configure complex systems in order to protect critical infrastructures against all manners of intrusion or vulnerability—we’re probably going to continue to see breaches caused by human error.
Phishing Continues to Evolve, But Reigns Supreme.
Phishing attacks are getting better and more sophisticated every year. Scams that started primarily via email in the 90’s to spread malware have become the most difficult challenge to address in modern cybersecurity. And phishing’s rate of success is actually on the rise.
In a report published earlier this year, Lookout found that the rate at which users fall victim to phishing attacks has increased by 85% every year since 2011. A study conducted by PhishMe found that 91% of all cyberattacks and resulting data breaches started with a phishing email. What’s more, mobile devices are 18x more likely to encounter a phishing attack than to inadvertently download mobile malware.
Despite a security focus on mobile and IoT devices—expect to see effective phishing attacks continue to dominate in the world of cybersecurity challenges. Newer forms of phishing scams have emerged using SMS (“SMiShing”) and Voice/phone calls (“Vishing”) and they are as effective as ever—bringing “traditionally understood” attacks onto new devices and formats that the general public aren’t aware of. Malicious actors are also increasingly relying on mobile and messaging apps to deliver “phishes”.
And if you think because you’re using an iPhone that you’re safe. You couldn’t be more wrong. Wandara found that mobile users on iOS suffer twice as many mobile phishing attacks as Android users. And as many as 25% of all web-based mobile phishing attacks come from games.
The takeaway here is to be wary and scrutinize all emails and links that you get. “Know before you go” to any link in your emails. And even if you receive a legitimate-looking email from a known contact, you’re better off manually going to the destination, rather than clicking on a link that could have malicious parameters or actually be a homograph attack. Phishing combined with social engineering efforts has proven the most difficult malicious trend to address. And we don’t see an end in sight. Definitely not in 2019.
On the bright side, we expect that the significant advancements made in AI research will help contribute to new and better technologies (and services) for identifying various forms of phishing scams.
Regulation For All. Fake News, Data Privacy, and Other Concerns.
It’s been a rough couple of years for tech giants and social media platforms—which have been under fire, not only for major data breaches, but for how loosely they’ve played with the personal information and data (think geolocation and shopping habits) of their users. The EU’s GDPR was a major response to problems that have been brewing for the past several years.
It’s also helped pave the way for regulation from other countries. Australia just passed an encryption bill that requires tech companies to comply with requests to unlock devices (and unencrypt data) from law enforcement agencies and government bodies. It’s already received widespread criticism from tech companies, who say it will have “significant and far-reaching consequences”. Chances are that Australia’s move will have global impacts on privacy. (What those are, we’ll have to wait and see.)
These regulations will continue to cause strain for tech companies in the coming year—as governing bodies exert increasing pressure.
With the U.S. presidential election cycle looming on the horizon and continued concerns over data privacy, we expect that tech and social platforms will receive a lot of continued attention from politicians and media outlets. We’ll continue to see the effects and consequences from these forms of regulation that play out on world stage.
The big question is how—particularly in democratic societies where the media and free press plays an important role—do we address challenges posed by “Fake News”, deep fakes, biases in the media, and what limitations do we place on platforms (social media and other) to maintain balance and trust within our own institutions?
But, It’s My Right… As a Smart Assistant.
Advancements in AI and automation have made virtual assistants and smart “chatbots” commonplace. And the advantage of these helpers and services are clear. They have the ability to far outperform any individual employee—communicating with thousands of people simultaneously and automating a growing number of jobs all over the world.
There’s been a lot of talk this year over the expression and free speed rights when considering bots. On September 30th, Jerry Brown of California signed regulations that requires that bots disclose that they are not human. The law won’t go into effect until July 1st, 2019—but it’s sure to make an impact on the online services and support tools that have grown in popularity in recent past.
And once again, it comes back to social media platforms. “The bill was really written around social media accounts, Twitter and Facebook bots in particular,” says Carl Landers, chief marketing officer of Conversica, which sells conversational bots for marketing and sales.
It’ll be interesting to see how this plays out, but in the meantime, we’re continuing with the development of enhanced capabilities to detect and block traffic from known bots.
The Ad Tech Industry’s Continued Lip Service to Ad Fraud Prevention
Ad fraud is still a major problem for the ad tech industry. In 2018, ad fraud worldwide is expected to exceed $19 billion USD (Statista), up from only $6.5 billion in 2016 (White Ops).
There have been some major positive events against ad fraud networks this past year. For instance, the International Bureau of Advertisers (IAB) ads.txt solution outlines how the industry can significantly reduce ad fraud caused by domain spoofing. It has seen significant adoption thanks in large part to Google. In late 2018, we also saw the takedown of 3ve, a massive ad fraud bot network that is believed to have stolen over $29 million from advertisers.
READ MORE: Major Ad Fraud Operation “3ve” Taken Down Thanks to Industry Collaboration
But ultimately, the ad tech industry is not doing enough to stem fraudulent activity. As advertisers are looking for new channels and ways to spend their budgets—fraudsters are similarly engineering new ways to take advantage of industry changes. Mobile and in-app fraud, for example, continues to rise. In 2018, it’s estimated that in-app fraud increased by as much as 800%.
We expect that, without additional intervention on part of ad tech platforms themselves, 2019 will be a banner year for ad fraud. AI and automated classification systems will be crucial in mitigating continued ad fraud on mobile—particularly for in-app advertisements and on other services as fraudsters shift their efforts in response to industry defenses. Ad tech platforms must invest in brand safety, botnet detection, and on-page traffic analytics tools in order to continue to mitigate fraud and prevent revenue losses.
IoT Security in the Home Remains Elusive.
The role of the Internet of Things (IoT) in our modern lives cannot be understated. From self-driving cars to edge computing, the IoT will play a significant role in revolutionizing nearly every industry.
For these industries and applications—security is a must and a “no brainer”.
IoT system and sensor failures within industrial and manufacturing equipment would cause damage to machines and danger to human workers—all undermining the advantages of IoT in the first place: productivity and efficiency. Critical infrastructure failures within our cities would have massive repercussions. Think of the chaos that would ensue if we were to allow malicious actors—including foreign governments—to compromise critical systems like our power grid, water/sanitation, communications, self-driving cars, medical devices, etc.
Businesses and governments are acutely aware of the cost associated with DDoS attacks and therefore willing to pay for security measures to protect themselves. IoT Tech Expo reports that DDoS attacks cost enterprises between $50,000 and $2.5M USD.
The consumer IoT market; however, is an entirely different story. Security has been overlooked for a variety of reasons:
- Associated costs
- Lack of demand
- Lack of regulation
- Lack of understanding technology & risk
It’s incredibly difficult to bring a “secured smart device” to market at a competitive price point when all of your competitor’s opt to forego security measures. Because of this, better “secured” devices typically lose to cheaper, “unsecured” functionally-equivalent devices.
On the regulation front, we did see some progress made in 2018. As of September, California signed into law the first IoT Cybersecurity Law for the United States—effectively requiring that any consumer connected device be outfitted with “reasonable security features”. Supporters believe it will “help everybody” even though “it probably doesn’t go far enough.” Meanwhile, critics have described it as a “typically bad bill based on a superficial understanding of cybersecurity/hacking that will do little improve security, while doing a lot to impose costs and harm innovation.”
Ultimately, we haven’t (yet) experienced a major security incident that has impacted consumers directly. And because of that most consumers aren’t aware of the risk. Until that changes, we won’t see a demand for security—and acceptance of higher prices. So for the time being, security takes a back seat in consumer IoT devices.
Because really… ”What’s the worst that’s going to happen if my $30 smart speaker gets compromised?” Will it cost another $30 to replace it? Will it eat up a few extra bucks in electricity costs when it happens?
The answers are… we don’t really know what the full extent of a major security breach would be.
We do know that unsecured IoT devices are “enslaved” by botnets and leveraged for DDoS attacks. And thanks to Project rIoT from UC Berkeley that quantified the associated costs of an IoT device compromised by Mirai Malware—we now know that the costs of increased energy consumption are passed on to the consumer.
We also know that thanks to the convenience of voice-controlled “connected” devices and appliances—IoT has seen rapid adoption within consumer homes. It’s now estimated that over 90% of consumer homes in the United States own a “smart device”. That is a lot of homes and devices that are ripe for the picking.
All of these events and trends lead us to the conclusion that… It’s highly likely that we’ll experience a major IoT security event 2019.
Conclusions
Overall, 2019 is shaping up to be an interesting year and we think these trends will play a significant role in the upcoming year. We know that this is hardly an exhaustive list. We’re also intently focused on advancements in artificial intelligence, deep learning, and neural machine translation (and how we apply them).
But we’ll leave that for another day.
Thanks for reading and Happy Holidays from zvelo!





