Fight Ransomware with a Defense in Depth Strategy
The daily average of Ransomware attacks, as observed by Check Point Research, has increased by 50% in Q3 compared to the first half of 2020. From government, to financial services, to hospitals — highly lucrative Ransomware attacks around the world have exploded and show no signs of relenting. As Ransomware attacks continue to make headlines, organizations must evolve towards fighting Ransomware with a Defense in Depth strategy.
Cybersecurity is aggressively evolving, and defenders are deeply engaged in a chess match against the attackers. Every step a defender takes to secure their network an attacker creates a new method or vector of attack. Defenders must continuously study their moves, closely observing indicators of compromise, learning to reliably predict potential strategies and attack vectors. These observations become part of a complex Defense in Depth strategy, used to identify security gaps or potential points of failure within the organization’s operating environment.
Common Tools for Cyber Defense
Defense in Depth leverages a range of security tools which offer varying types of protection throughout the different access points of the environment. Below are some of the most commonly used to address the primary security layers.
Firewalls
Since Ransomware attacks begin with the Malicious Cyber Actor (MCA) gaining access to a network, a firewall is often the first line of defense. The firewall blocks certain ports from accessing the network, and uses behavioral and/or rule based detections to stop an MCA from gaining access to the network.
Network Intrusion Prevention System (NIDS)
NIDS provide another layer of security by using behavioral and rule based detection for potential Ransomware threats at the network level. Additionally, NIDS are equipped to provide the data granularity necessary for cyber analysts to detect an attack so that they can respond with a targeted approach to block the MCA from accessing the network.
Endpoint Detection and Response (EDR)
EDRs provide crucial visibility for network security teams to detect threats, like Ransomware, if the MCAs manage to evade the other security layers and penetrate the network. EDRs provide host based detection, investigation and remediation against malware to contain threats before the nefarious actions of an MCA can be fully executed.
Patch Management
Patch Management is another layer of preventative security and serves to prevent compromises before they even happen. Ransomware attackers will target system vulnerabilities which can be used to escalate privileges and gain remote code execution on the system without admin privileges.
Logging and Network Segmentation
Logging and Network Segmentation serves as an additional obstacle for MCAs once they have penetrated the other network security tools. If an MCA does compromise the network, this is used to segment specific areas of the network to mitigate the movement of an attack, slowing it down until defenders are able to contain the threat. In the case of Ransomware attacks, this would be leveraged to prevent lateral movement within the network.
While the above security tools offer a solid broad based defense against threats and exploits, they are also outmatched against skilled MCAs — notably when it comes to Ransomware attacks. So what’s missing from the Defense in Depth tool set? And how can defenders bolster security to get ahead of the Ransomware attacks?
The short answer is cyber threat intelligence. The most commonly missing element of a Defense in Depth strategy is having both comprehensive cyber threat intelligence and a dedicated team of security professionals who understand how to derive actionable threat intelligence from what would otherwise just be potentially useful data about threats. While many organizations may source one, or several OSINT or commercial threat intelligence feeds, they often lack the internal resources to truly understand how that data impacts their unique environment. When it comes to cybersecurity, it’s crucial for threat intelligence data to be viewed based on the unique makeup of an organization’s operating environment
A Ransomware Example: Emotet
The image below shows data which identifies a commonly used piece of malware called Emotet. This malware is designed as a trojan that allows attackers to gain remote access to a system, exploit it and install other malicious payloads, especially Ransomware.
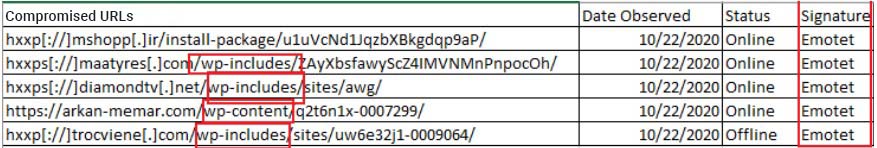
Gaining extra insight into attackers C2 and malicious domains can give defenders another layer of defense to prevent an attack or provide the detection capability so that defenders have the ability to respond to an attack.
Based on the data presented above, a threat intelligence professional may be able to identify domain squatting or typosquatting if an attacker is targeting your companies or clients, as well as an MCA’s C2 and new techniques being used in a campaign. However, identification is only one step. Once the potential threat is identified, a defender would need to validate the C2 infrastructure and hopefully glean new malware hashes or attack vectors — details which would be used to disrupt the kill chain and block MCAs at the initial access point. This demonstrates the difference between just having threat intelligence data, and having actionable threat intelligence data.
Whether your organization is facing Ransomware attacks, or any of the other legions of threats and exploits, the single most valuable addition to your threat defense is curated threat intelligence. While the threat of Cyber Attacks remain a top concern for organizations, relatively few take the preventative action required to secure their environment and train security personnel. At least, not until after they’ve been attacked — which is far more costly than if they had taken preventative measures to begin with.





