Revisiting DNS RPZ
Since the release of BIND 9 in 2010, RPZ has proven a powerful technology for security and network management—allowing organizations to implement an additional DNS configuration layer. In fact, BIND is the most widely used Domain Name System software on the internet—making RPZ configuration options like integrating commercial feeds, blocklists, and URL databases like zveloDB™ all the more attractive. So let’s take a moment to revisit the advantages of RPZ.
RPZ (Response Policy Zone) is a technology developed by ISC (Internet Systems Consortium) for use with BIND (Berkeley Internet Name Domain) enabling custom handling for collections of domains (zones).
Effectively, RPZ is a DNS Firewall and filtering mechanism, allowing you to assign specific actions for DNS recursive resolvers to perform when requests are made—and thereby giving you custom control over your network and user traffic.
Control is security, and RPZ can be implemented to improve network security, combat DNS misuse, and help filter out content from sources you don’t want on your network. This provides an additional layer of protection and customization on top of whatever DNS service you may use. RPZ zone files can be configured to manage a variety of policies (e.g. malicious, objectionable, bit errors, specific categories) allowing you to reroute—or simply block—requests to domains within such policies.
How RPZ Works
RPZ takes DNS resolutions made by your DNS service and then compares them against your RPZ configuration files—where you are able to organize domains/IPs into policies and manage how they are handled.
The image below demonstrates how users on your network make DNS requests and how those requests are processed.
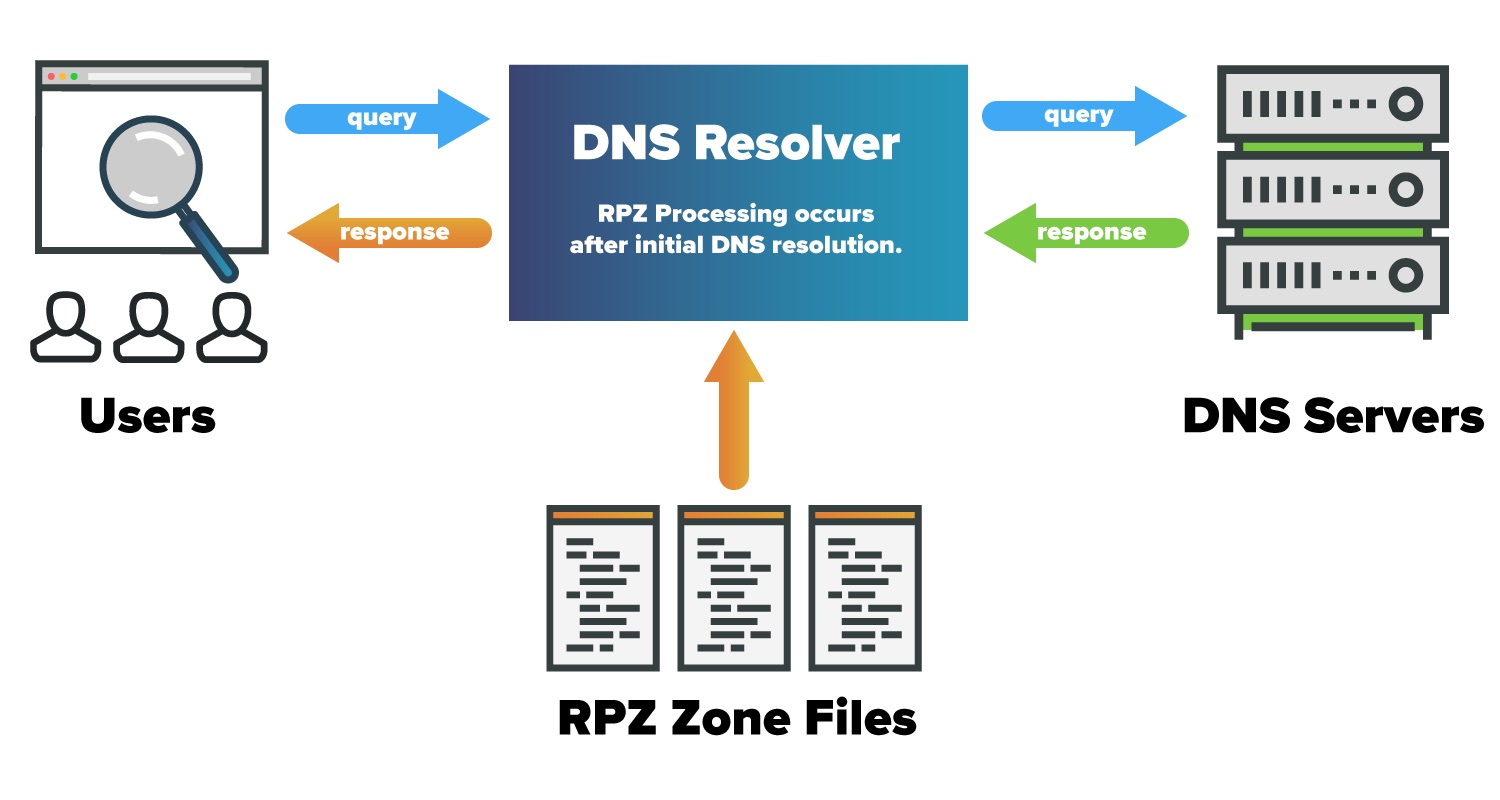
Where does RPZ live in the DNS ecosystem? First the request passes through your network gateway and to your DNS Filtering provider where it is resolved and returned. The response comes back to your own DNS Resolver (e.g. BIND) where it is compared with your existing zone files. Based on matches within those files, the result is processed (allowed, blocked, changed, etc.) accordingly and passed along to the user.
What are the advantages of that, you might ask? Well, if your company subscribes to data feeds for URL categories, malicious sources, etc. you could pull those domains and IPs into a zone policy that meets your needs—creating a modular separation between your network security framework (policies) and the malicious sources. That would make it easy for your IT team to customize your DNS handling while leveraging a variety of cybersecurity feeds from industry leaders, such as zvelo.
It also gives you the freedom to manage policies how you see fit. For example, if you subscribe to a number of feeds that curate and monitor phishing sites (Anti-Phishing Work Group for instance)—you would be able to incorporate (and merge as you see fit) those feeds into a unified “phishing” policy zone policy. You could outright block those phishing sites—or if you prefer—redirect users to a “walled garden”, thereby informing the user of the danger and educating them against future compromises.
The benefits extend beyond malicious sources. Alternatively, you may wish to treat pornographic sites (NSFW) or social media platforms differently—and reroute traffic to an internal page describing your company policies to employees who attempt to access certain content.
Those are just a couple of examples illustrating the possibilities for managing requests. But what are some of the other uses?
Common Configurations & Uses for DNS RPZ
The advantage of RPZ is that it enables you to configure and fine-tune DNS handling to your specific needs and based on other resources and feeds your company has access to. Some common configurations and zone file setups include:
Whitelist Domains
There are IPs and resources that you know are secure and need to be “always on” in order for employees to access online services and business to function normally. You can create a zone file to “whitelist” domains and ensure that these DNS requests are always allowed.
Block Known Malicious Sources
There are a number of feeds and blocklists available that curate known malicious sources (C&C, distribution points, phishing sites, etc.). An effective way to protect your networks is to create a zone file that handles known malicious sources—whether redirecting the request or blocking outright. zvelo’s Malicious Detection dataset, for example, curates and analyzes millions of known ActiveWeb malicious sources across 10 malicious categories.
Redirect Domains (e.g. Protection Against Bitsquatting and Bit Errors.)
“Bitsquatting” or “Cybersquatting” is the practice of registering a domain name that is one bit off from a legitimate domain—typically for the purpose of spoofing and phishing attacks. DNS RPZ can be configured to protect internal traffic.
Redirect Infected Users to a Walled Garden
In some cases, a user may not know that their machine is infected. However, their computer may begin making DNS requests to a malicious C&C source. Fortunately, with RPZ you can redirect that activity—and the user—to a “walled garden” informing them of the infection so that the malware can be quarantined/removed.
Block Objectionable Content
NSFW! Whether for blocking access on an enterprise network or enabling parents to set controls for their kids internet surfing—zone files can be created to block or redirect content that is considered pornography, child abuse, terrorism, hate speech, violence, or any other of the almost 500 categories zvelo supports.
Proxies & Passthroughs
Perhaps a DNS request is made to a source that is new to the internet, and therefore uncategorized. You may wish to configure your network to block these entirely (if security is the priority)—or (functionality is the priority) a passthrough that allows traffic to continue while the request is forwarded for in-depth analysis and categorization.
Additional Thoughts
As with all network security measures, there are pros and cons to different implementations and all should be carefully considered to avoid performance pitfalls, false positives, and unintended security gaps.
Similar to zvelo’s category mappings, DNS RPZ allows you to select and customize the handling of DNS requests based on your needs. Used in coordination with a categorization solution like the zveloDB™ URL Database that supports nearly 500 distinct content, objectionable, and malicious categories—RPZ offers top-tier flexible configuration options and advanced security. The impact of DNS misuse and other malicious tactics online can be damaging and debilitating to any organization, but RPZ is a technology that can be used to mitigate threats and secure your networks.
Want to learn more about selecting and implementing categories and DNS zones that meet your requirements? Stay tuned for our next blog on implementing Response Policy Zones and using them to protect against malicious threats. If you’re interested in learning more about our categorization capabilities, you can check our zveloDB™ URL Database or our Malicious Detection capabilities.
Contact zvelo Sales for more information, or to schedule an evaluation.





