The global economy for cybercrime is booming — reportedly generating revenues of 1.5 trillion USD annually. Soaring ransomware profits bankrolled by easy targets, and growing demand for cyber insurance to fuel the extortion economy, are emboldening cyber criminals to capitalize on the business of ransomware operations through Ransomware-as-a-Service (RaaS).
Ransomware in 2020
In January of this year, cybersecurity organizations reported ransomware among the top threats to keep an eye on during 2020 — anticipating the upward trend over the last quarter of 2019 to continue escalating. So far, those predictions are proving accurate.
Ransomware trends show that attackers have moved from mass consumer attacks to highly targeted campaigns against businesses and government organizations. This shift towards larger, more profitable ransomware targets, is referred to as Big Game Hunting (BGH). Some of this year’s BGH attacks so far include California-based Communications & Power Industries (CPI), a defense contractor, was hit up for a $500,000 ransom in January. The Reading Municipal Light Department (RMLD) was also hit by cyber criminals who took down the electricity provider’s website to extort payment from them Legal services giant Epiq Global was hit in February, followed by Visser, a parts manufacturer for Tesla and SpaceX. Most recently, Cognizant was hit with a Maze Ransomware attack mid April.
Factors Contributing to Ransomware Escalation
Higher Ransom Payouts
Global ransomware reports have the cost to victims ranging anywhere from $6 Billion USD all the way up to $25 Billion USD, with the average demand set at around $85,000 USD. As the trend shows an increase in BGH, those costs are predicted to surge as high as $170 Billion USD in 2020.
Easy Targets
Lax security policies, lack of disaster recovery plans, failure to encrypt sensitive data, failure to invest in prevention & detection — These are just some of the things that make organizations easy targets for the Malicious Cyber Actors (MCAs). And now, as organizations across the globe shift to a remote workforce due to the Coronavirus pandemic, the field of opportunity for MCAs to carry out RaaS attacks is wide open.
Growing Cyber Insurance Market
Based on data from ransomware attacks which have been reported, organizations with cyber insurance are more inclined to just pay off a ransom. While cyber insurance is a good idea for the organizations, it also increases the likelihood for an attack to receive the ransom demand which further incentivizes attacks.
What is Ransomware-as-a-Service?
Overview
Ransomware-as-a-Service (RaaS) businesses sell or rent out compact, easy-to-deploy, and scalable malware kits to individuals or groups who want to stage cyber attacks. These RaaS kits are typically promoted and sold on the dark web using the same marketing and sales tactics that legitimate businesses use. Those who access the dark web will find a plethora of ads displayed in underground forums promoting different ransomware kits at different price points with varying degrees of service. Just like a legitimate SaaS offering, ransomware-as-a-service malware portals can include discounts, bundled offers, around-the-clock support, user reviews, forums and more. The cost for a RaaS kit can range anywhere from around $40 up and scale upwards into the thousands. Even at a cost of thousands, the cost of the ransomware kit is nominal when attackers see the potential to claim a high dollar ransom from a BGH target.
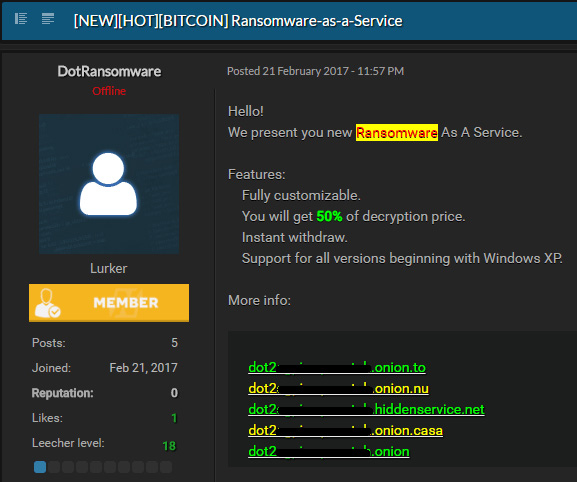
How Does Ransomware-as-a-Service Work?
Revenue Models
Ransomware-as-a-service operators use the same types of revenue models as legitimate businesses. Some operators will sell their services for a flat fee, or monthly subscriptions. Others choose to use the profit sharing model. While the success rate for ransom attacks (based on the number of attempts) is estimated to be quite low, profit sharing allows for the RaaS operators the opportunity to draw larger profits, albeit less consistently. Regardless, this is a popular revenue model so we can assume the profits are enough for the operator to sustain its services. Affiliate programs are another channel for RaaS operators to generate revenue. Like all other aspects of ransomware-as-a-service — aside from the criminal intent, of course — the affiliate programs function in the same way as legitimate SaaS businesses, taking a cut of the profits.
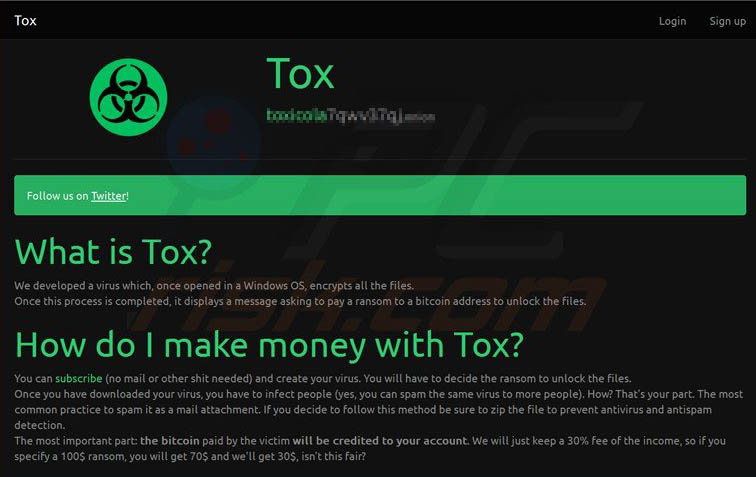
Ease of Use
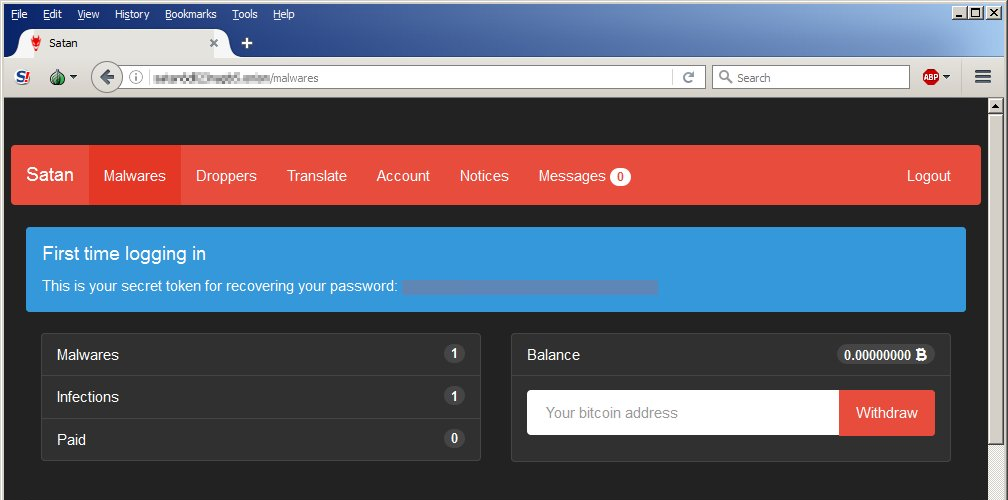
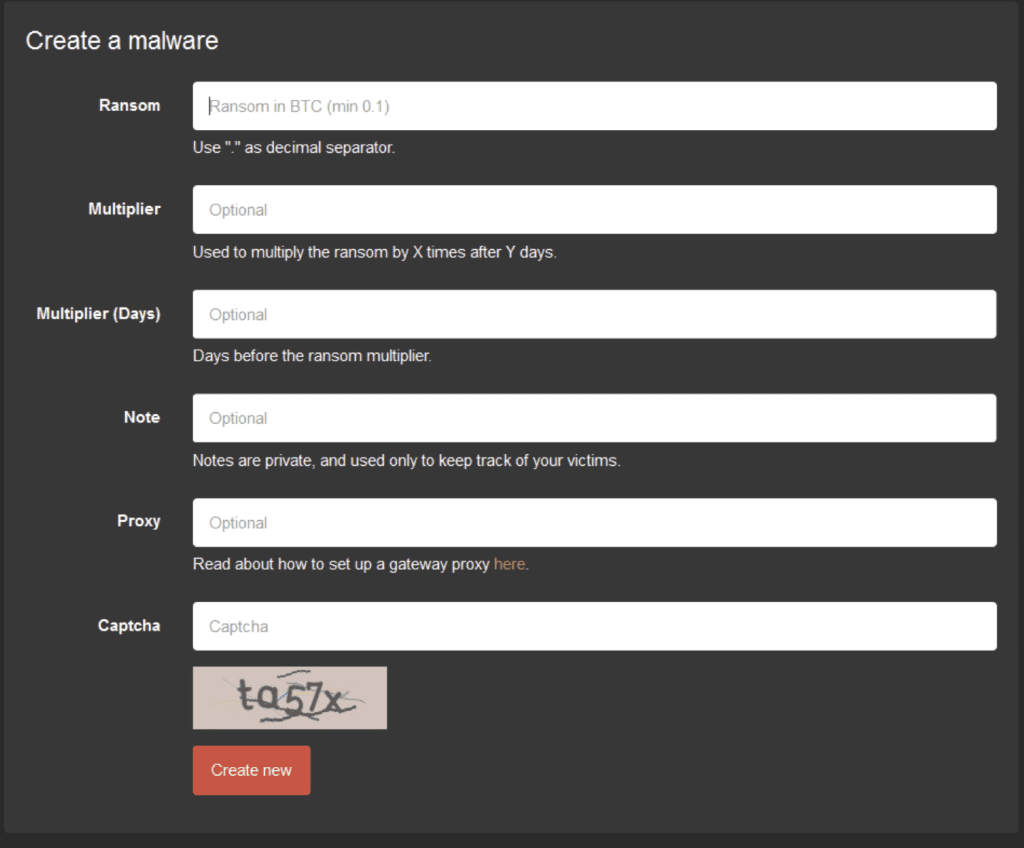
Again, similar to the legitimate SaaS models, the appeal of ransomware-as-a-service is the ease of use. If a person has access to the dark web, signing up for and setting up a ransomware attack is no more difficult than creating an account with any other service provider. You select a package based on price and services included, create an account login, add some criteria to the type of malware you wish to create, and then you’re set. Shown below, is one example.
The Wild Card: Coronavirus
By almost all accounts, security companies across the board predicted an increase in ransomware attacks during 2020. None of those predictions, however, took into account the complete global upheaval due to the Coronavirus pandemic. While zvelo does not currently have predictions specific to how Coronavirus will impact the ransomware, or RaaS businesses, the cybersecurity team does have data showing an uptick in coronavirus related domain registrations and observed malicious redirectors.
While the full impact of this pandemic specific to ransomware and RaaS operations remains to be seen, we continue to recommend that people remain hypervigilant and make every effort they can to make themselves a hard target. Please see our recent post for best security practices and tips for remote workers during COVID-19 and make sure your organization is taking steps to implement security measures.





