zveloCTI and The Value of Curated Cyber Threat Intelligence
In today’s highly competitive cybersecurity markets, where speed and veracity of threat detections are critical to providing effective customer protection, the quality of threat data is critical. The techniques used by the top-tier cyber threat intel firms to ‘curate’ their data are closely held proprietary trade secrets and the reasons for the considerable differences in coverage, lift and speed of threat detections by the premium providers and the also-rans. Said differently, not all threat data is curated equally and the differences can result in an organization receiving comprehensive protection, while another company’s CISO and team are in emergency react mode responding to the latest breach, social engineering, or ransomware attack. Oftentimes, we find that some curated threat intelligence data is really nothing more than the aggregation of several of the leading open source and/or commercial threat feeds — with the ‘curation’ piece referring to a select group of threat feeds. Since the definition of what constitutes ‘curated’ threat intel feeds vs aggregated threat intel feeds varies depending on the source, it can be challenging to quantify the value of curated cyber threat intelligence because the results of curation can vary widely. When you are looking at threat intelligence solutions and evaluating threat feeds, it’s crucial to understand what goes into the curation process before you can assess the potential value of curated threat intelligence to your organization.
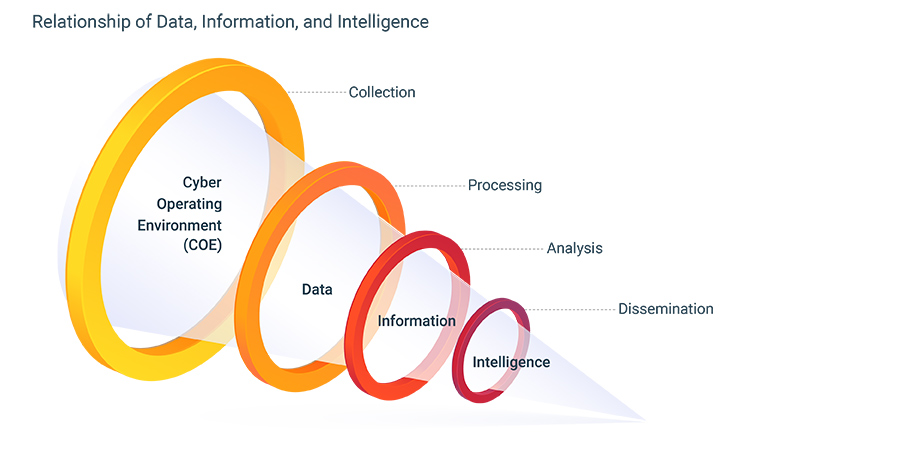
To better demonstrate the value of curation that zvelo offers, we’ll use the Cyber Threat Intelligence Feedback Loop as a framework for explaining some of the key pieces in the curation process. For zvelo, the bulk of the curation process spans the following phases: Collection, Processing, Validation, Analysis, and Feedback.
CTI Collection
zvelo collects billions of data points across the ProActiveWeb, ActiveWeb, and InActiveWeb, in addition to its own proprietary threat detections, zvelo integrates multiple proprietary sources, open source and third party threat feeds so your organization benefits from having a single source collecting as much threat intelligence data as possible. zvelo’s supported coverage includes active web traffic from 600+ million users across the globe, supplying the volume, visibility, and location data required to observe MCAs and potential threats as early as possible. These potential early detections provide key insights as the data moves into the processing phase.
CTI Processing
CTI Processing starts with data aggregation and normalization. An organization must aggregate all the threat feeds data into a single information set which can then be placed into a common schema. This is a critical step as the CTI Analysis stage is dependent upon aggregation and normalization for the pattern analysis, assessment, and scoring which will ultimately produce actionable cyber threat intelligence from the raw data. Once the data has been aggregated and normalized, zvelo processes it into information bins for web content categorization, suspicious new domain registrations, malicious detections, and phishing detections, where the data will then be validated.
Data Validation
Data validation is a crucial step in the process which can significantly enhance the value of curation by creating actionable intelligence from massive amounts of raw data. Unfortunately, it’s also frequently skipped. Just because (pick an input, internal source, third-party feed, crowdsourced, etc.) one source claims something is malicious/phishing/evil, it may or may not be accurate. And, while it may have been accurate weeks earlier, not all threats detected are active threats. A lack of thorough validation, can lead to high false positives and lower quality threat data across the board.
zvelo’s methodology for CTI processing uses a balanced mix of rules-based, human supervised AI/ML, and manual analysis by its expert Cybersecurity Team. The blended approach to CTI processing and validation ensures that our meticulously curated cyber threat intelligence feeds deliver more unique detections, faster and more accurately than other threat feeds on the market.
CTI Analysis
The next step in the curation process is analysis. Throughout the course of a single day, zvelo analyzes several hundred million URLs using a hybrid analysis model. As part of the analysis, zvelo includes rich metadata attributes which are valuable for contextual relevance, forensic lookback, and incident response — just to name a few. zvelo maintains a multi-disciplinary team to conduct manual analysis when automated analysis is unable to provide an acceptable outcome.
Once the data moves through analysis, the end result is high veracity threat intelligence feeds which can be immediately ingested into customer products or network defense systems to break the cyber kill chain by disrupting a variety of MITRE ATT&CK techniques in their Cyber Operating Environment (COE).
CTI Feedback
The final piece of the CTI process involved in curation is feedback. In practical terms, feedback is a dialogue between the intelligence producer and the intelligence consumer, or customer. Feedback should be collaborative. Producers must be willing to listen to feedback and the customer must be willing to offer it. Feedback should also be push and pull. In other words, the customer should push feedback to the producer and the producer should proactively reach out to the customer to pull feedback.
Feedback can also be viewed as helping the CTI producer to assess the value of the products delivered. This assessment is typically viewed in two bins:
- Measure of Performance (MOP): Quantitative metrics on how much/how many CTI products were produced and delivered.
- Measure of Effectiveness (MOE): Qualitative assessment of how well the CTI products produced and delivered fulfilled organizational requirements.
Analyzing both MOP and MOE feedback can help the CTI producer tune their pipeline to ensure the most actionable intelligence is delivered, thereby maximizing the value of curation.
zvelo is a highly collaborative organization that regularly reviews feedback from our customers. For example, zvelo maintains 24/7 coverage of our web content categorization efforts to quickly review and correct any classification errors. zvelo’s threat feeds include methods for both interactive and offline feedback from customers. We measure both MOP and MOE for threat feeds and drive that information back into the CTI process for loop continuation. This ensures that zvelo continuously refines collections to stay ahead of Malicious Cyber Actors (MCAs).
CTI and the Real World Value of Curated Threat Intelligence Feeds
The value of curated cyber threat intelligence delivered via zveloCTI’s threat feeds is clearly demonstrated by how those curated threat feeds perform against the competition:
- 100% Coverage of existing threat detections
- 40% Lift in new and unique threat detections
- 65% Faster detections
In the end, the reasons to procure curated cyber threat intelligence, as well as the resulting value will vary from one organization to the next. In many cases, curated threat intel is critical to efficient threat protection. And for some, it may be a significant cost savings from not having to manage the infrastructure and human resources required to collect and process massive volumes of data. For others, the value of curated threat intelligence may be found in operational efficiencies by streamlining the number of threat intelligence sources and reducing the workload for normalizing and standardizing the raw data for processing. And many other organizations that lack the internal resources to perform the threat analysis will discover value through the direct performance results, reduced cyber risk and improved threat posture. Much like how threat intelligence is uniquely valuable to each individual environment, so is the value of curated cyber threat intelligence. Maximizing the value to your organization ultimately hinges upon curation.